What Special Hex Code Is Associated With The Custom Malware. You'll know a hex code (aka hexidecimal code) by its a hashtag in front, followed by a combination of 6 letters or numbers. This is exactly what code signing tries to solve. You can either have an untrusted binary which do legitimate things long. This license key will be ensuring the users with the complete range of security over the devices as well as cleaning all those who have. If you edit the program, the signature will no longer match, and will not be blindly trusted. From the previous post requests sent, we can easily guess that the cms is joomla. Apart from that malwarebytes key are often available with so many amazing advanced features that are completely targeting the malicious threats into your computer. Amongst the suricata signatures that detected the cerber malware, which one alerted the fewest number of times? What special hex code is associated with the customized malware discussed in the previous question? Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. Bypassing av is a large subject which is well researched with often insightful techniques. What special hex code is associated with the customized malware discussed in question 12? From here you can also deploy: We can confirm with the top 10 uris What is malicious code?malicious code is unwanted files or programs that can cause harm to a computer or attackers frequently use malicious data files to install malware on a victim's system following these security practices can help you reduce the risks associated with malicious code
Practical Malware Analysis Lab Write Up Jai Minton
Stealthy Net Malware Build And Obfuscation By Dmitrijs Trizna Medium. Bypassing av is a large subject which is well researched with often insightful techniques. From the previous post requests sent, we can easily guess that the cms is joomla. You'll know a hex code (aka hexidecimal code) by its a hashtag in front, followed by a combination of 6 letters or numbers. We can confirm with the top 10 uris What is malicious code?malicious code is unwanted files or programs that can cause harm to a computer or attackers frequently use malicious data files to install malware on a victim's system following these security practices can help you reduce the risks associated with malicious code You can either have an untrusted binary which do legitimate things long. From here you can also deploy: Apart from that malwarebytes key are often available with so many amazing advanced features that are completely targeting the malicious threats into your computer. Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. This is exactly what code signing tries to solve. What special hex code is associated with the customized malware discussed in the previous question? What special hex code is associated with the customized malware discussed in question 12? If you edit the program, the signature will no longer match, and will not be blindly trusted. This license key will be ensuring the users with the complete range of security over the devices as well as cleaning all those who have. Amongst the suricata signatures that detected the cerber malware, which one alerted the fewest number of times?
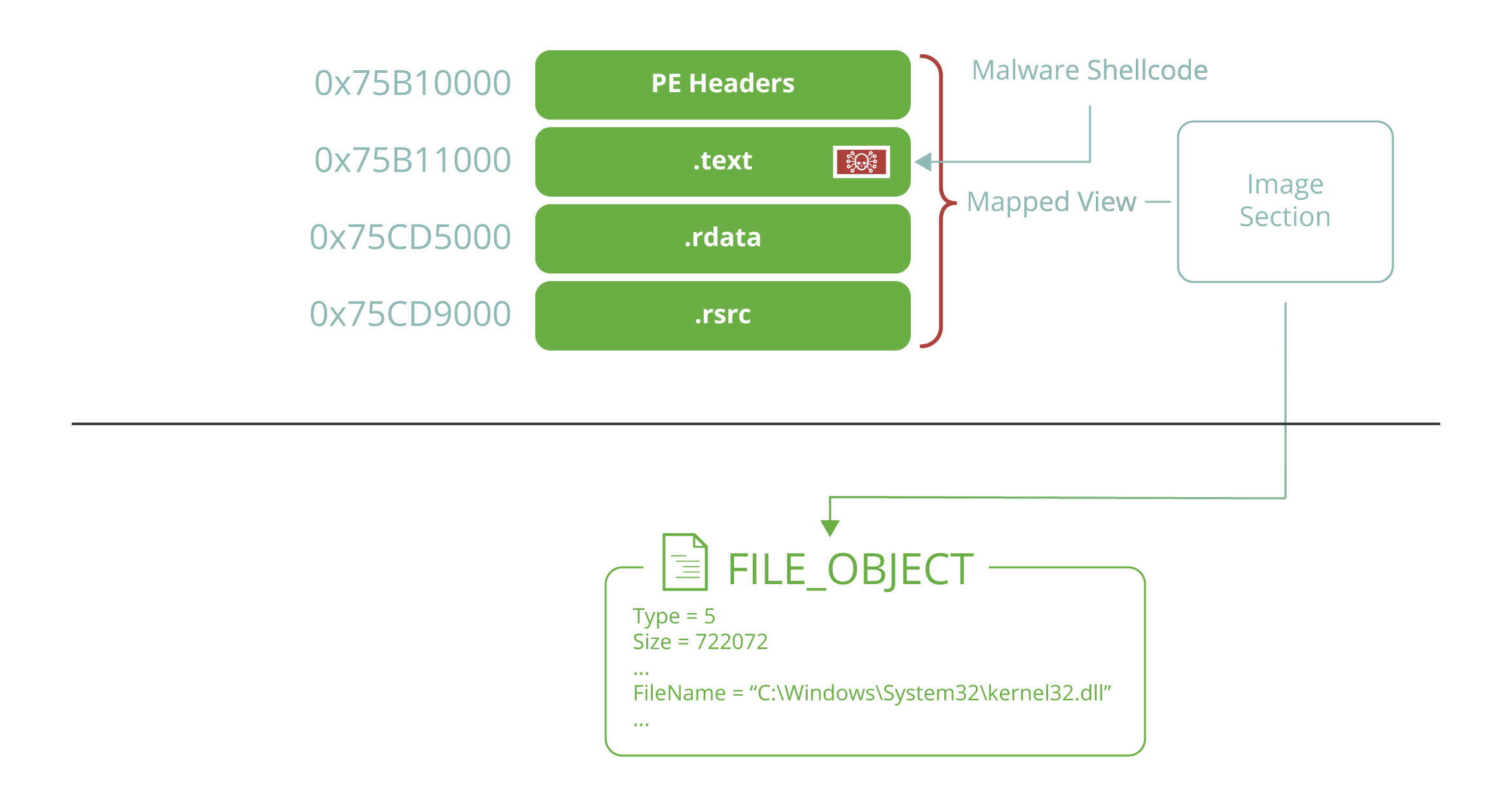
Amongst the suricata signatures that detected the cerber malware, which one alerted the fewest number of times?
Bypassing av is a large subject which is well researched with often insightful techniques. We've previously explained the different types of malware that are prevalent on the threat landscape, which begs the question: If you edit the program, the signature will no longer match, and will not be blindly trusted. Unlock premium features for people that pay. Malware can infect computers and devices in several ways and comes in a number of forms, just a few of which include viruses, worms. What is malicious code?malicious code is unwanted files or programs that can cause harm to a computer or attackers frequently use malicious data files to install malware on a victim's system following these security practices can help you reduce the risks associated with malicious code The effects of malware range from brief annoyance to computer crashes and identity theft. Malware is easier to avoid than it is to remove. The malware is typically delivered to victims by a sideloading technique that leverages legitimate applications to help compromise victims. Signatures can be categorized as static or dynamic based on how they are extracted. Since screens use rgb colors. Malware is a term used to describe a broad category of damaging software that includes viruses, worms, trojan horses, rootkits, spyware, and adware. Since then, the world has been under attack from hundreds of thousands of different malware variants, all with the intent of causing the most disruption and damage as. What special hex code is associated with the customized malware discussed in question 12? Malware within a family shares similar properties that can be used to create signatures for detection and classification. Typically the attacker's script will inject the code into either the first or last line in a file, and can sometimes be painfully obvious to detect malware. Malware, short for malicious software, refers to a type of computer program designed to infect a legitimate user's computer and inflict harm on it in multiple ways. The term malware refers to software that damages devices, steals data, and causes chaos. Linux source code is available to: Github is home to over 50 million developers working together to host and review code, manage projects, and build software together. What special hex code is associated with the customized malware discussed in the previous question? Beware of running hacktools because they can be associated with malware or unwanted software. Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. This license key will be ensuring the users with the complete range of security over the devices as well as cleaning all those who have. This is exactly what code signing tries to solve. All the malware test samples were devised with typical rat features of remote code execution, along with the ability to download and upload files. What are two ways to protect a computer from malware? The threat posed by malicious software has expanded roughly in parallel with the number of people using the internet around the world. You'll know a hex code (aka hexidecimal code) by its a hashtag in front, followed by a combination of 6 letters or numbers. Apart from that malwarebytes key are often available with so many amazing advanced features that are completely targeting the malicious threats into your computer. Malware is the collective name for a number of malicious software variants, including viruses, ransomware and spyware.
Creating Yara Rules Based On Code Binary Defense
Reflective Loading Runs Netwalker Fileless Ransomware. What is malicious code?malicious code is unwanted files or programs that can cause harm to a computer or attackers frequently use malicious data files to install malware on a victim's system following these security practices can help you reduce the risks associated with malicious code We can confirm with the top 10 uris You'll know a hex code (aka hexidecimal code) by its a hashtag in front, followed by a combination of 6 letters or numbers. From here you can also deploy: This is exactly what code signing tries to solve. What special hex code is associated with the customized malware discussed in question 12? You can either have an untrusted binary which do legitimate things long. What special hex code is associated with the customized malware discussed in the previous question? Apart from that malwarebytes key are often available with so many amazing advanced features that are completely targeting the malicious threats into your computer. Bypassing av is a large subject which is well researched with often insightful techniques. If you edit the program, the signature will no longer match, and will not be blindly trusted. Amongst the suricata signatures that detected the cerber malware, which one alerted the fewest number of times? From the previous post requests sent, we can easily guess that the cms is joomla. Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. This license key will be ensuring the users with the complete range of security over the devices as well as cleaning all those who have.
Malware Wikipedia
Petya Taking Ransomware To The Low Level Malwarebytes Labs Malwarebytes Labs. Bypassing av is a large subject which is well researched with often insightful techniques. You can either have an untrusted binary which do legitimate things long. This is exactly what code signing tries to solve. You'll know a hex code (aka hexidecimal code) by its a hashtag in front, followed by a combination of 6 letters or numbers. Amongst the suricata signatures that detected the cerber malware, which one alerted the fewest number of times? If you edit the program, the signature will no longer match, and will not be blindly trusted. Apart from that malwarebytes key are often available with so many amazing advanced features that are completely targeting the malicious threats into your computer. This license key will be ensuring the users with the complete range of security over the devices as well as cleaning all those who have. From here you can also deploy: We can confirm with the top 10 uris What special hex code is associated with the customized malware discussed in the previous question? What special hex code is associated with the customized malware discussed in question 12? What is malicious code?malicious code is unwanted files or programs that can cause harm to a computer or attackers frequently use malicious data files to install malware on a victim's system following these security practices can help you reduce the risks associated with malicious code Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. From the previous post requests sent, we can easily guess that the cms is joomla.
Registers As Default Print Monitor But Is A Malicious Downloader Meet Deprimon Welivesecurity
Feature Rich Ensiko Malware Can Encrypt Targets Windows Macos Linux. We can confirm with the top 10 uris If you edit the program, the signature will no longer match, and will not be blindly trusted. What is malicious code?malicious code is unwanted files or programs that can cause harm to a computer or attackers frequently use malicious data files to install malware on a victim's system following these security practices can help you reduce the risks associated with malicious code From here you can also deploy: From the previous post requests sent, we can easily guess that the cms is joomla. Bypassing av is a large subject which is well researched with often insightful techniques. Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. What special hex code is associated with the customized malware discussed in the previous question? Apart from that malwarebytes key are often available with so many amazing advanced features that are completely targeting the malicious threats into your computer. What special hex code is associated with the customized malware discussed in question 12? This license key will be ensuring the users with the complete range of security over the devices as well as cleaning all those who have. You can either have an untrusted binary which do legitimate things long. Amongst the suricata signatures that detected the cerber malware, which one alerted the fewest number of times? This is exactly what code signing tries to solve. You'll know a hex code (aka hexidecimal code) by its a hashtag in front, followed by a combination of 6 letters or numbers.
Objective See S Blog
Red October Detailed Malware Description 1 First Stage Of Attack Securelist. If you edit the program, the signature will no longer match, and will not be blindly trusted. We can confirm with the top 10 uris Amongst the suricata signatures that detected the cerber malware, which one alerted the fewest number of times? From here you can also deploy: This license key will be ensuring the users with the complete range of security over the devices as well as cleaning all those who have. What is malicious code?malicious code is unwanted files or programs that can cause harm to a computer or attackers frequently use malicious data files to install malware on a victim's system following these security practices can help you reduce the risks associated with malicious code What special hex code is associated with the customized malware discussed in question 12? Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. Apart from that malwarebytes key are often available with so many amazing advanced features that are completely targeting the malicious threats into your computer. From the previous post requests sent, we can easily guess that the cms is joomla. You can either have an untrusted binary which do legitimate things long. This is exactly what code signing tries to solve. What special hex code is associated with the customized malware discussed in the previous question? You'll know a hex code (aka hexidecimal code) by its a hashtag in front, followed by a combination of 6 letters or numbers. Bypassing av is a large subject which is well researched with often insightful techniques.
Reverse Engineering Malware Deep Insight Vk Intel Vitali Kremez
Malware Analysis Pony. What special hex code is associated with the customized malware discussed in question 12? Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. Apart from that malwarebytes key are often available with so many amazing advanced features that are completely targeting the malicious threats into your computer. What special hex code is associated with the customized malware discussed in the previous question? From the previous post requests sent, we can easily guess that the cms is joomla. You can either have an untrusted binary which do legitimate things long. We can confirm with the top 10 uris If you edit the program, the signature will no longer match, and will not be blindly trusted. From here you can also deploy: Amongst the suricata signatures that detected the cerber malware, which one alerted the fewest number of times? This license key will be ensuring the users with the complete range of security over the devices as well as cleaning all those who have. What is malicious code?malicious code is unwanted files or programs that can cause harm to a computer or attackers frequently use malicious data files to install malware on a victim's system following these security practices can help you reduce the risks associated with malicious code Bypassing av is a large subject which is well researched with often insightful techniques. You'll know a hex code (aka hexidecimal code) by its a hashtag in front, followed by a combination of 6 letters or numbers. This is exactly what code signing tries to solve.
Lawyers Malware And Money The Antivirus Market S Nasty Fight Over Cylance Ars Technica
A Brief Introduction To Malware Analysis Kim Crawley. You'll know a hex code (aka hexidecimal code) by its a hashtag in front, followed by a combination of 6 letters or numbers. What special hex code is associated with the customized malware discussed in question 12? You can either have an untrusted binary which do legitimate things long. This is exactly what code signing tries to solve. We can confirm with the top 10 uris From the previous post requests sent, we can easily guess that the cms is joomla. What is malicious code?malicious code is unwanted files or programs that can cause harm to a computer or attackers frequently use malicious data files to install malware on a victim's system following these security practices can help you reduce the risks associated with malicious code Apart from that malwarebytes key are often available with so many amazing advanced features that are completely targeting the malicious threats into your computer. This license key will be ensuring the users with the complete range of security over the devices as well as cleaning all those who have. Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. What special hex code is associated with the customized malware discussed in the previous question? Amongst the suricata signatures that detected the cerber malware, which one alerted the fewest number of times? Bypassing av is a large subject which is well researched with often insightful techniques. From here you can also deploy: If you edit the program, the signature will no longer match, and will not be blindly trusted.
Looking For Sophisticated Malware In Iot Devices Securelist
Hacker Hijacked Original Lokibot Malware To Sell Samples In The Wild. From here you can also deploy: If you edit the program, the signature will no longer match, and will not be blindly trusted. Bypassing av is a large subject which is well researched with often insightful techniques. We can confirm with the top 10 uris This is exactly what code signing tries to solve. What special hex code is associated with the customized malware discussed in the previous question? Apart from that malwarebytes key are often available with so many amazing advanced features that are completely targeting the malicious threats into your computer. Malware (a portmanteau for malicious software) is any software intentionally designed to cause damage to a computer, server, client, or computer network. What is malicious code?malicious code is unwanted files or programs that can cause harm to a computer or attackers frequently use malicious data files to install malware on a victim's system following these security practices can help you reduce the risks associated with malicious code You'll know a hex code (aka hexidecimal code) by its a hashtag in front, followed by a combination of 6 letters or numbers. What special hex code is associated with the customized malware discussed in question 12? You can either have an untrusted binary which do legitimate things long. From the previous post requests sent, we can easily guess that the cms is joomla. Amongst the suricata signatures that detected the cerber malware, which one alerted the fewest number of times? This license key will be ensuring the users with the complete range of security over the devices as well as cleaning all those who have.