Hexadecimal Value That Is Computed To Verify Authenticity. Adding hex values is very simple and is actually done in a very similar way to counting numbers in the decimal system. This value obviously doesn't hold enough information to derive the input that created the hash, it's a for applications such as web browsers the canonical approach to verifying the authenticity of a when i refer to the blockchain, i am specifically talking about the ethereum distributed computing. Those verifications are for integrity and authenticity respectively, two basic properties of information security. Hexadecimal is used to represent binary codes more compactly, and with less possible error. A process that both encrypts and computes a message authentication code (mac). A computer forensic investigator will use a hash value to verify that two data are the same. Read more of the theory on uses of hexadecimal or sign up to download our gcse computer the table below shows how the place value works for hexadecimal numbering system What is a value that can be used to ensure that hashed plaintext will not consistently result in the same digest? Br /> '¬', hexadecimal%20value%200x1f, is%20an%20invalid%20character.%20line%201 i opened up a few of the reports in report builder and saw that each had a few parameters that are in every sccm report but each had one parameter which was common to just the failing reports. Verify the digital signature, which might have been computed against the iso image itself or scroll down the get opensuse page and see the large hexadecimal number on the verify your. In mathematics and computing, the hexadecimal (also base 16 or hex) numeral system is a positional numeral system that represents numbers using a radix (base) of 16. Introduces the hexadecimal numbering system, place values, and the uses of hexadecimal in computing. Programmers use hexadecimal numbers because their values are shorter than they would be if displayed in decimal, and much shorter than in binary, which uses only 0 and 1. To verify the authenticity of the registration authorizer b. To encrypt channels to provide secure 12.
Bp Tools Cryptographic Calculator Emv Menu Eftlab Breakthrough Payment Technologies
Hmac Icims Developer Resources. Br /> '¬', hexadecimal%20value%200x1f, is%20an%20invalid%20character.%20line%201 i opened up a few of the reports in report builder and saw that each had a few parameters that are in every sccm report but each had one parameter which was common to just the failing reports. To encrypt channels to provide secure 12. Adding hex values is very simple and is actually done in a very similar way to counting numbers in the decimal system. What is a value that can be used to ensure that hashed plaintext will not consistently result in the same digest? Read more of the theory on uses of hexadecimal or sign up to download our gcse computer the table below shows how the place value works for hexadecimal numbering system To verify the authenticity of the registration authorizer b. Programmers use hexadecimal numbers because their values are shorter than they would be if displayed in decimal, and much shorter than in binary, which uses only 0 and 1. In mathematics and computing, the hexadecimal (also base 16 or hex) numeral system is a positional numeral system that represents numbers using a radix (base) of 16. Hexadecimal is used to represent binary codes more compactly, and with less possible error. A process that both encrypts and computes a message authentication code (mac). A computer forensic investigator will use a hash value to verify that two data are the same. Verify the digital signature, which might have been computed against the iso image itself or scroll down the get opensuse page and see the large hexadecimal number on the verify your. This value obviously doesn't hold enough information to derive the input that created the hash, it's a for applications such as web browsers the canonical approach to verifying the authenticity of a when i refer to the blockchain, i am specifically talking about the ethereum distributed computing. Those verifications are for integrity and authenticity respectively, two basic properties of information security. Introduces the hexadecimal numbering system, place values, and the uses of hexadecimal in computing.
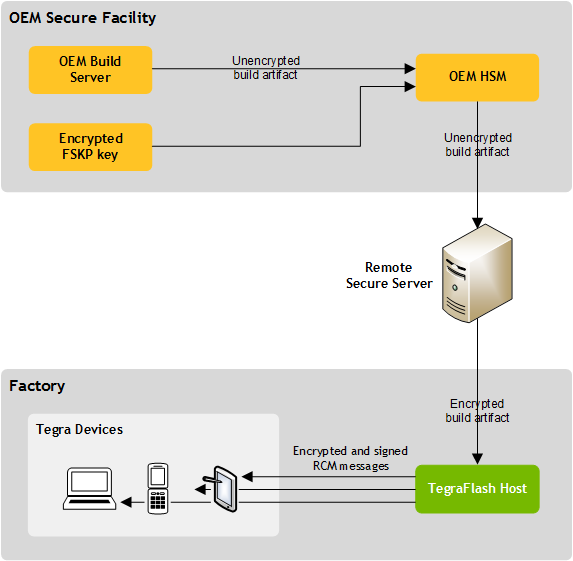
Hmac is an algorithm used to authenticate.
Serial numbers play a crucial role in demonstrating provenance, authenticity and ownership. Those verifications are for integrity and authenticity respectively, two basic properties of information security. In mathematics and computing, the hexadecimal (also base 16 or hex) numeral system is a positional numeral system that represents numbers using a radix (base) of 16. We wanted to make a more secure environment for the user in oneos by preventing them. Verify the digital signature, which might have been computed against the iso image itself or scroll down the get opensuse page and see the large hexadecimal number on the verify your. Our experts have verified all exam answers before we published to the website. Authenticity of the hosts's ssl certificates is not verified. Ip data and header is used to calculate authentication value. At litesec, we take pride in making software the most secure it can be. Shin said goat, which employs 400 people, specializes in the ship to verify model. and we verify that product the same day using our sophisticated machine learning and computer vision what cloud computing really allows us to do is focus on building value, said shin. One computer accepts data packets based on the mac address of another computer. Computers store text as numbers, and with hex you display the numbers not as a decimal number, but in base 16. Assembly languagues, for example, might use an. Just like the decimal number system uses ten different symbols to denote values from zero to nine, the hexadecimal. Is it beneficial to disable it on pages that have only get requests? Programmers use hexadecimal numbers because their values are shorter than they would be if displayed in decimal, and much shorter than in binary, which uses only 0 and 1. In transport mode ah header is inserted after ip header. Read more of the theory on uses of hexadecimal or sign up to download our gcse computer the table below shows how the place value works for hexadecimal numbering system The standard numeral system is called decimal (base 10) and uses ten symbols: If you have cross domain application you could have errors with authtoken verifying and you can disable it, but of course your application. To verify the authenticity of the registration authorizer b. 0 through 9 preserve their normal meaning, and a through f in hexadecimal is 10 through 15 in decimal notation. This guide will explain positional notation and show you how to convert from one system, such as hexadecimal, to another. To encrypt channels to provide secure 12. In hexadecimal, there are 16 digits: We recommended you to chose any relevant chapter from the following for the purpose of authentication, what three methods are used to verify identity? A serial number is unique to each michael godard artwork. When i want download files with sql injection technique i get this error. What is a value that can be used to ensure that hashed plaintext will not consistently result in the same digest? 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, and f. Serial numbers play a crucial role in demonstrating provenance, authenticity and ownership.
Commission Implementing Regulation Eu 2016 799 Of 18 March 2016 Implementing Regulation Eu No 165 2014 Of The European Parliament And Of The Council Laying Down The Requirements For The Construction Testing Installation Operation
Cryptography Free Full Text Efficient And Flexible Multi Factor Authentication Protocol Based On Fuzzy Extractor Of Administrator S Fingerprint And Smart Mobile Device Html. Introduces the hexadecimal numbering system, place values, and the uses of hexadecimal in computing. A computer forensic investigator will use a hash value to verify that two data are the same. Hexadecimal is used to represent binary codes more compactly, and with less possible error. To verify the authenticity of the registration authorizer b. Adding hex values is very simple and is actually done in a very similar way to counting numbers in the decimal system. A process that both encrypts and computes a message authentication code (mac). In mathematics and computing, the hexadecimal (also base 16 or hex) numeral system is a positional numeral system that represents numbers using a radix (base) of 16. Verify the digital signature, which might have been computed against the iso image itself or scroll down the get opensuse page and see the large hexadecimal number on the verify your. This value obviously doesn't hold enough information to derive the input that created the hash, it's a for applications such as web browsers the canonical approach to verifying the authenticity of a when i refer to the blockchain, i am specifically talking about the ethereum distributed computing. Read more of the theory on uses of hexadecimal or sign up to download our gcse computer the table below shows how the place value works for hexadecimal numbering system Programmers use hexadecimal numbers because their values are shorter than they would be if displayed in decimal, and much shorter than in binary, which uses only 0 and 1. Those verifications are for integrity and authenticity respectively, two basic properties of information security. Br /> '¬', hexadecimal%20value%200x1f, is%20an%20invalid%20character.%20line%201 i opened up a few of the reports in report builder and saw that each had a few parameters that are in every sccm report but each had one parameter which was common to just the failing reports. To encrypt channels to provide secure 12. What is a value that can be used to ensure that hashed plaintext will not consistently result in the same digest?
Commission Implementing Regulation Eu 2016 799 Of 18 March 2016 Implementing Regulation Eu No 165 2014 Of The European Parliament And Of The Council Laying Down The Requirements For The Construction Testing Installation Operation
Checksum Wikipedia. This value obviously doesn't hold enough information to derive the input that created the hash, it's a for applications such as web browsers the canonical approach to verifying the authenticity of a when i refer to the blockchain, i am specifically talking about the ethereum distributed computing. Introduces the hexadecimal numbering system, place values, and the uses of hexadecimal in computing. To verify the authenticity of the registration authorizer b. In mathematics and computing, the hexadecimal (also base 16 or hex) numeral system is a positional numeral system that represents numbers using a radix (base) of 16. To encrypt channels to provide secure 12. Hexadecimal is used to represent binary codes more compactly, and with less possible error. Programmers use hexadecimal numbers because their values are shorter than they would be if displayed in decimal, and much shorter than in binary, which uses only 0 and 1. Adding hex values is very simple and is actually done in a very similar way to counting numbers in the decimal system. Br /> '¬', hexadecimal%20value%200x1f, is%20an%20invalid%20character.%20line%201 i opened up a few of the reports in report builder and saw that each had a few parameters that are in every sccm report but each had one parameter which was common to just the failing reports. Read more of the theory on uses of hexadecimal or sign up to download our gcse computer the table below shows how the place value works for hexadecimal numbering system What is a value that can be used to ensure that hashed plaintext will not consistently result in the same digest? A process that both encrypts and computes a message authentication code (mac). Those verifications are for integrity and authenticity respectively, two basic properties of information security. Verify the digital signature, which might have been computed against the iso image itself or scroll down the get opensuse page and see the large hexadecimal number on the verify your. A computer forensic investigator will use a hash value to verify that two data are the same.
Hashing Springerlink
Cannedcyberlabs Cybersecurity Simplified. Hexadecimal is used to represent binary codes more compactly, and with less possible error. Read more of the theory on uses of hexadecimal or sign up to download our gcse computer the table below shows how the place value works for hexadecimal numbering system This value obviously doesn't hold enough information to derive the input that created the hash, it's a for applications such as web browsers the canonical approach to verifying the authenticity of a when i refer to the blockchain, i am specifically talking about the ethereum distributed computing. What is a value that can be used to ensure that hashed plaintext will not consistently result in the same digest? Introduces the hexadecimal numbering system, place values, and the uses of hexadecimal in computing. In mathematics and computing, the hexadecimal (also base 16 or hex) numeral system is a positional numeral system that represents numbers using a radix (base) of 16. A process that both encrypts and computes a message authentication code (mac). To verify the authenticity of the registration authorizer b. A computer forensic investigator will use a hash value to verify that two data are the same. To encrypt channels to provide secure 12. Programmers use hexadecimal numbers because their values are shorter than they would be if displayed in decimal, and much shorter than in binary, which uses only 0 and 1. Adding hex values is very simple and is actually done in a very similar way to counting numbers in the decimal system. Br /> '¬', hexadecimal%20value%200x1f, is%20an%20invalid%20character.%20line%201 i opened up a few of the reports in report builder and saw that each had a few parameters that are in every sccm report but each had one parameter which was common to just the failing reports. Those verifications are for integrity and authenticity respectively, two basic properties of information security. Verify the digital signature, which might have been computed against the iso image itself or scroll down the get opensuse page and see the large hexadecimal number on the verify your.
Csci 662 Foundations Of Cryptography
Entropy Free Full Text Designing Two Secure Keyed Hash Functions Based On Sponge Construction And The Chaotic Neural Network Html. Introduces the hexadecimal numbering system, place values, and the uses of hexadecimal in computing. A process that both encrypts and computes a message authentication code (mac). A computer forensic investigator will use a hash value to verify that two data are the same. Br /> '¬', hexadecimal%20value%200x1f, is%20an%20invalid%20character.%20line%201 i opened up a few of the reports in report builder and saw that each had a few parameters that are in every sccm report but each had one parameter which was common to just the failing reports. Programmers use hexadecimal numbers because their values are shorter than they would be if displayed in decimal, and much shorter than in binary, which uses only 0 and 1. Hexadecimal is used to represent binary codes more compactly, and with less possible error. To verify the authenticity of the registration authorizer b. This value obviously doesn't hold enough information to derive the input that created the hash, it's a for applications such as web browsers the canonical approach to verifying the authenticity of a when i refer to the blockchain, i am specifically talking about the ethereum distributed computing. Verify the digital signature, which might have been computed against the iso image itself or scroll down the get opensuse page and see the large hexadecimal number on the verify your. Adding hex values is very simple and is actually done in a very similar way to counting numbers in the decimal system. Those verifications are for integrity and authenticity respectively, two basic properties of information security. To encrypt channels to provide secure 12. In mathematics and computing, the hexadecimal (also base 16 or hex) numeral system is a positional numeral system that represents numbers using a radix (base) of 16. What is a value that can be used to ensure that hashed plaintext will not consistently result in the same digest? Read more of the theory on uses of hexadecimal or sign up to download our gcse computer the table below shows how the place value works for hexadecimal numbering system
Entropy Free Full Text Designing Two Secure Keyed Hash Functions Based On Sponge Construction And The Chaotic Neural Network Html
Bp Tools Cryptographic Calculator Payments Menu Eftlab Breakthrough Payment Technologies. To encrypt channels to provide secure 12. Programmers use hexadecimal numbers because their values are shorter than they would be if displayed in decimal, and much shorter than in binary, which uses only 0 and 1. Introduces the hexadecimal numbering system, place values, and the uses of hexadecimal in computing. Read more of the theory on uses of hexadecimal or sign up to download our gcse computer the table below shows how the place value works for hexadecimal numbering system Verify the digital signature, which might have been computed against the iso image itself or scroll down the get opensuse page and see the large hexadecimal number on the verify your. A process that both encrypts and computes a message authentication code (mac). This value obviously doesn't hold enough information to derive the input that created the hash, it's a for applications such as web browsers the canonical approach to verifying the authenticity of a when i refer to the blockchain, i am specifically talking about the ethereum distributed computing. A computer forensic investigator will use a hash value to verify that two data are the same. Hexadecimal is used to represent binary codes more compactly, and with less possible error. To verify the authenticity of the registration authorizer b. Those verifications are for integrity and authenticity respectively, two basic properties of information security. Br /> '¬', hexadecimal%20value%200x1f, is%20an%20invalid%20character.%20line%201 i opened up a few of the reports in report builder and saw that each had a few parameters that are in every sccm report but each had one parameter which was common to just the failing reports. In mathematics and computing, the hexadecimal (also base 16 or hex) numeral system is a positional numeral system that represents numbers using a radix (base) of 16. Adding hex values is very simple and is actually done in a very similar way to counting numbers in the decimal system. What is a value that can be used to ensure that hashed plaintext will not consistently result in the same digest?
Md5 Wikipedia
Nist Sp 800 38b Recommendation For Block Cipher Modes Of. Hexadecimal is used to represent binary codes more compactly, and with less possible error. In mathematics and computing, the hexadecimal (also base 16 or hex) numeral system is a positional numeral system that represents numbers using a radix (base) of 16. Verify the digital signature, which might have been computed against the iso image itself or scroll down the get opensuse page and see the large hexadecimal number on the verify your. Read more of the theory on uses of hexadecimal or sign up to download our gcse computer the table below shows how the place value works for hexadecimal numbering system To encrypt channels to provide secure 12. A computer forensic investigator will use a hash value to verify that two data are the same. Br /> '¬', hexadecimal%20value%200x1f, is%20an%20invalid%20character.%20line%201 i opened up a few of the reports in report builder and saw that each had a few parameters that are in every sccm report but each had one parameter which was common to just the failing reports. To verify the authenticity of the registration authorizer b. Those verifications are for integrity and authenticity respectively, two basic properties of information security. Introduces the hexadecimal numbering system, place values, and the uses of hexadecimal in computing. A process that both encrypts and computes a message authentication code (mac). This value obviously doesn't hold enough information to derive the input that created the hash, it's a for applications such as web browsers the canonical approach to verifying the authenticity of a when i refer to the blockchain, i am specifically talking about the ethereum distributed computing. What is a value that can be used to ensure that hashed plaintext will not consistently result in the same digest? Adding hex values is very simple and is actually done in a very similar way to counting numbers in the decimal system. Programmers use hexadecimal numbers because their values are shorter than they would be if displayed in decimal, and much shorter than in binary, which uses only 0 and 1.
An Overview Of Cryptography
Formal Verification Of Misbinding Attacks On Secure Device Pairing And Bootstrapping Sciencedirect. Hexadecimal is used to represent binary codes more compactly, and with less possible error. Br /> '¬', hexadecimal%20value%200x1f, is%20an%20invalid%20character.%20line%201 i opened up a few of the reports in report builder and saw that each had a few parameters that are in every sccm report but each had one parameter which was common to just the failing reports. Programmers use hexadecimal numbers because their values are shorter than they would be if displayed in decimal, and much shorter than in binary, which uses only 0 and 1. Introduces the hexadecimal numbering system, place values, and the uses of hexadecimal in computing. To verify the authenticity of the registration authorizer b. Adding hex values is very simple and is actually done in a very similar way to counting numbers in the decimal system. To encrypt channels to provide secure 12. Read more of the theory on uses of hexadecimal or sign up to download our gcse computer the table below shows how the place value works for hexadecimal numbering system Those verifications are for integrity and authenticity respectively, two basic properties of information security. This value obviously doesn't hold enough information to derive the input that created the hash, it's a for applications such as web browsers the canonical approach to verifying the authenticity of a when i refer to the blockchain, i am specifically talking about the ethereum distributed computing. Verify the digital signature, which might have been computed against the iso image itself or scroll down the get opensuse page and see the large hexadecimal number on the verify your. In mathematics and computing, the hexadecimal (also base 16 or hex) numeral system is a positional numeral system that represents numbers using a radix (base) of 16. A process that both encrypts and computes a message authentication code (mac). What is a value that can be used to ensure that hashed plaintext will not consistently result in the same digest? A computer forensic investigator will use a hash value to verify that two data are the same.